Wireshark 🦈
Network analyzer
Forensics
Network packet captures form a major part of forensic analysis and/or network vulnerability analysis. Majority of the CTF challenges include atleast one or more levels that involve some form of packet capture analysis.
Such packet capture files can be distinctly identified from their extensions that generally include either of the below:
.pcap.pcapng.cap
For a comprehensive list of output formats that are supported by Wireshark, refer here.
Table of contents
Installing Wireshark
On standard Linux distributions Wireshark can be installed from their respective package managers as shown below.
# In Ubuntu linux distros
## Add repository
sudo add-apt-repository universe
## Install package
sudo apt install wireshark
# In CentOS linux distros
## Install dependencies
yum install gtk
yum install libpcap
yum install tcpdump
## Install wireshark terminal and GUI
yum install wireshark
yum install wireshark-common
Most of the Kali Linux distributions already have Wireshark pre-installed in them. This is the preferred Linux distro for pen-testing and other security usages.
On Windows and MacOS the official website provides the required binaries for installation. Follow the steps to install Wireshark.
Learn the UI navigation
The UI of Wireshark is intuitive and easy to get used to. I will provide a high level overview of the UI here.
The initial screen shows the interfaces which are detected by wireshark, each of which can be configured to intercept packages. This mode of wireshark is more useful for network based challenges where we need to intercept the traffic between our box and a challenge server. But often, this mode is more useful for penetration testing a product and less during a CTF.
The mode we are concerned with, is analysis of packet capture files. To use this, you can open the capture file from the File > Open menu of Wireshark. Any of the Wireshark supported formats can be opened using this method.
Below is the UI we see after opening any supported packet capture file:
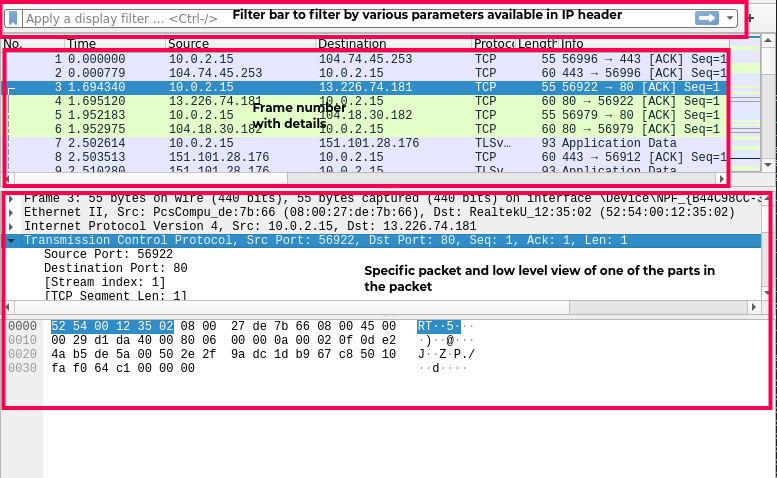
The major areas are explained in the image above. The filter area is mainly used to apply a plethora of protocol specific filters that are available in Wireshark. An exhaustive reference for the same can be found here. Supported protocols and protocol specific reference can be found here.
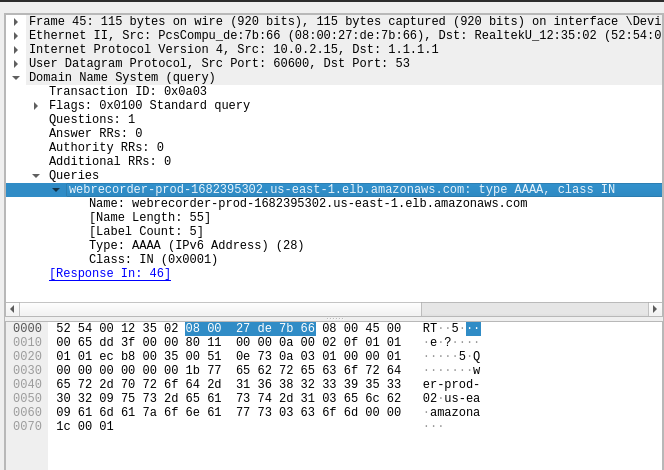
For each frame/packet, the segments of the packet are shown clearly as per the protocol stack. The layer wise segments along with protocol specific extensions are parsed and rendered in an easy to view structure. The same can be found below as an example for the DNS query packet.
Encrypted traffic data
As more and more protocols are coming in their encrypted variants, there is more and more possibility of encrypted traffic being intercepted and the need to analyze such traffic. We all know encrypted traffic is secure and cannot be parsed as shown above without the availability of key exchange files.
For packet captures which involves protocols like HTTPs, WSS, SSH we need to necessarily have the key exchange files. A snippet of the contents of such a file is shown below:
┌──(cryptonic㉿cryptonic-kali)-[~/CTFs/csawquals/contactus]
└─$ cat sslkeyfile.txt
# SSL/TLS secrets log file, generated by NSS
CLIENT_HANDSHAKE_TRAFFIC_SECRET 6c1621c245ea87f5f3f12e6d0d444e5da40d166183ead7b38e0f71c40fdd0487 9a298f859ef049436c6f2579808d9e26b2c1f2457f713342768b8a5273671e90
SERVER_HANDSHAKE_TRAFFIC_SECRET 6c1621c245ea87f5f3f12e6d0d444e5da40d166183ead7b38e0f71c40fdd0487 d28b6511a33b5132a7dc7add52fb2d6fdfb01a951b987225227edffd19c31759
CLIENT_HANDSHAKE_TRAFFIC_SECRET 783b909129ce9ffe54592fd731b42e95682e6fd49789947a5952b63887b882d2 6b63548cd0eb92092e8747d3f47b5b87bade6901120d69d28263a62a98ba9013
SERVER_HANDSHAKE_TRAFFIC_SECRET 783b909129ce9ffe54592fd731b42e95682e6fd49789947a5952b63887b882d2 a3c1e1f4f7e3cc4343f476c3a5dbfdb09a7f9f92838b1590e6f6098eaff62b90
The file basically enumerates the secret keys exchanged in the Diffie-Hellman, three way handshake done while establishing a secure channel for the underlying application protocol. Such a file is either upfront given along with a pcap file that contains encrypted traffic or is obfuscated away in some other file left with clues to be found.
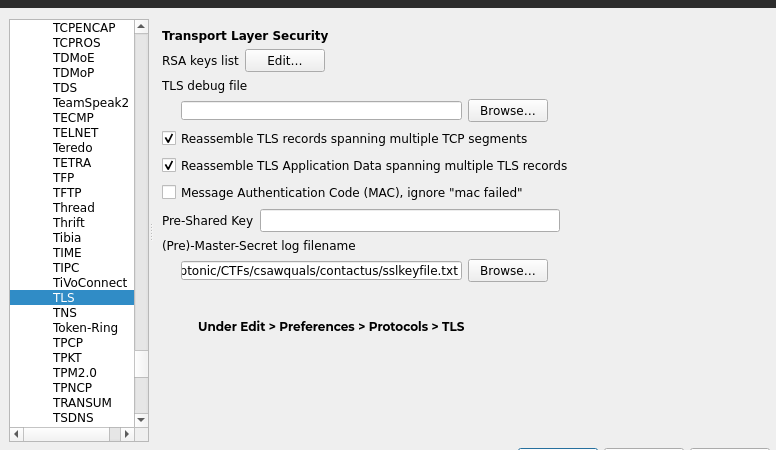
Once we have the key file we can import it in the UI by navigating to Edit > Preferences > Protocols > TLS > (Pre)-Master-Secret log filename. There are also many other settings which can be used based on the encryption mechanisms used in tehe traffic captured. Below image highlights the TLS sslkeyfile loading to decrypt any protocol working over TCP stack.
For a more detailed account on wireshark please refer any of the below:
- https://www.lifewire.com/wireshark-tutorial-4143298
- http://cobweb.cs.uga.edu/~perdisci/CSCIx250-F15/Slides/wireshark_lecture.pdf