A capture of the flag 🪧
Forensics
This is a basic forensics challenge which involves analysis of a .pcap file. A PCAP file is a network packet capture file that records all the packet transmissions that has occurred in the system for the duration of the capture.
Complete challenge description can be viewed here and the challenge file can be downloaded here.
This means the flag is hidden in one of the packets captured in this file. A PCAP file can be easily analyzed using Wireshark.
On loading the PCAP file we find that there are lot of packets captured. An organized way to go through the capture is to follow the inverse network layer, starting with the application layer first. This means we should tend to analyzed any specific application layer protocol packets like HTTP, HTTPs, SSH etc first.
Quickly we can see that Packet 247 which is an HTTP packet with a string parameter msg whose value seems to be Base-64 encoded. Such encoding techniques are common in order to bypass any flat search knowing the flag format. So its always best to not ignore encoded content, but to ensure whether it is an intended flag or not.
A screen shot of the packet is shown below:
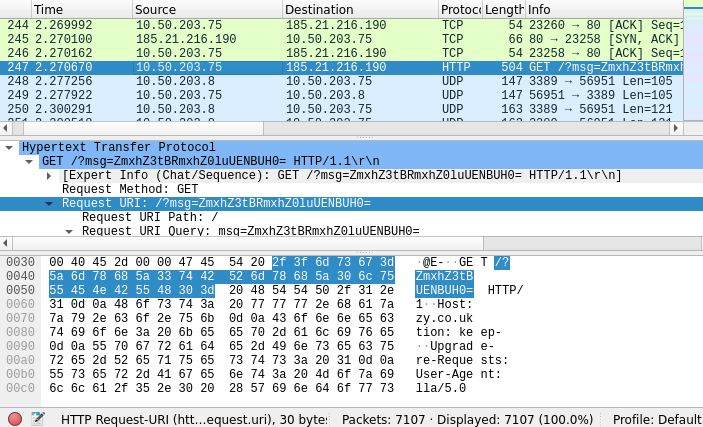
The Base 64 encoded value is: ZmxhZ3tBRmxhZ0luUENBUH0=
Decoding it we get the flag : flag{AFlagInPCAP}